Setup CloudTrail
Regle leverages S3 notification via AWS Lambda for ingesting CloudTrail logs.
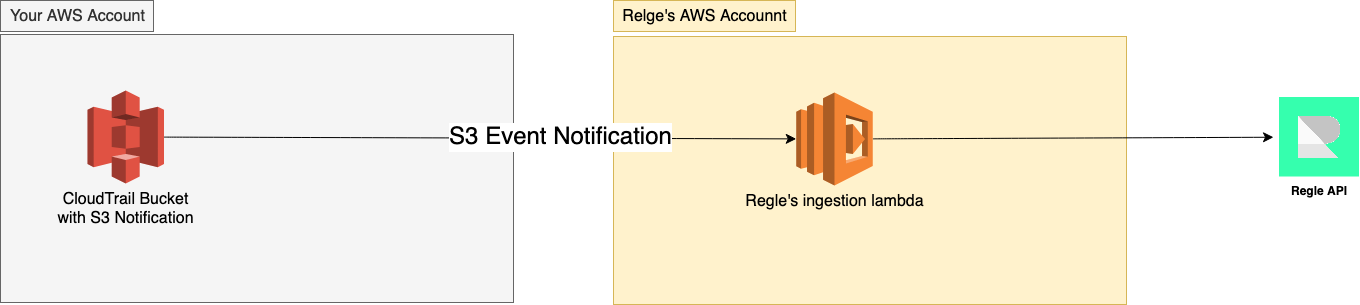
Follow the steps below to complete the integration.
Note, CloudTrail integration requires Regle account to be on Team or Businss Plan. To upgrade, please reach out via here.
Getting Started
1. Turn on CloudTrail in Your AWS Account
Enable CloudTrail on your AWS account by following the instructions here.
Note down the S3 bucket name hosting the CloudTrail log.
2. Configure Regle
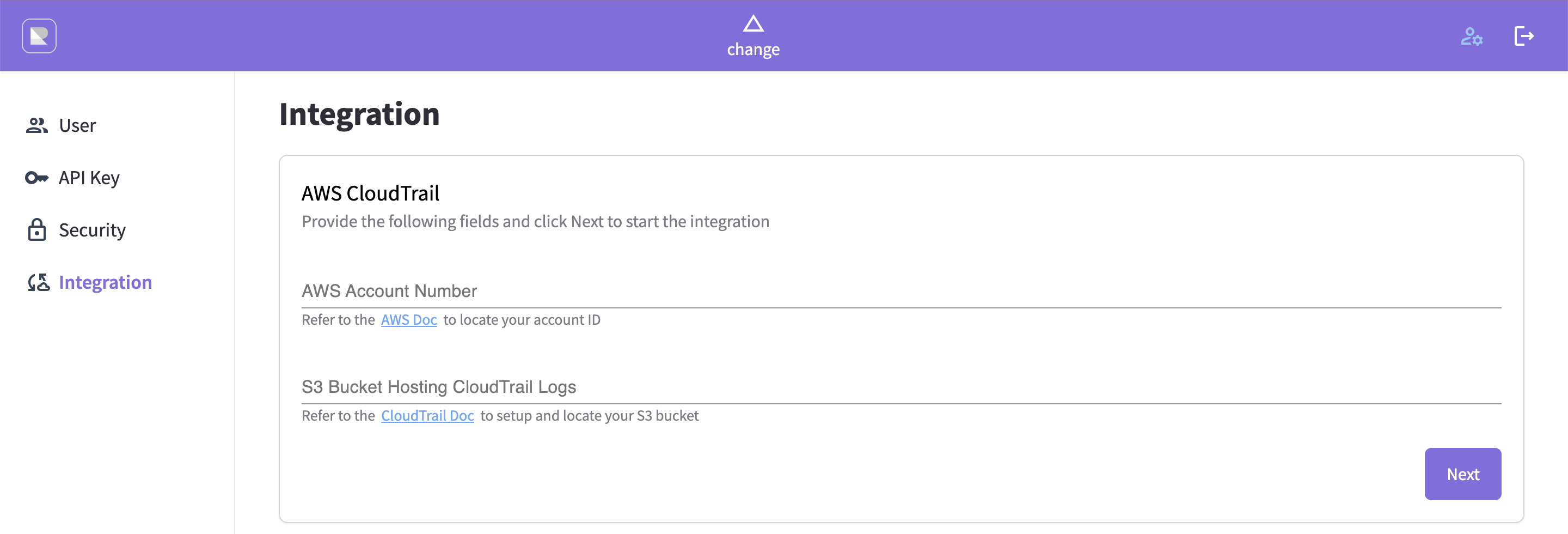
Now navigate to Regle > Admin Page > Integration > AWS CloudTrail, provide your AWS Account ID and S3 bucket name from step 1 and click "Next".
After saving successfully, Regle will create an AWS lambda function along with an AWS IAM Role and display their ARN in the Regle UI.
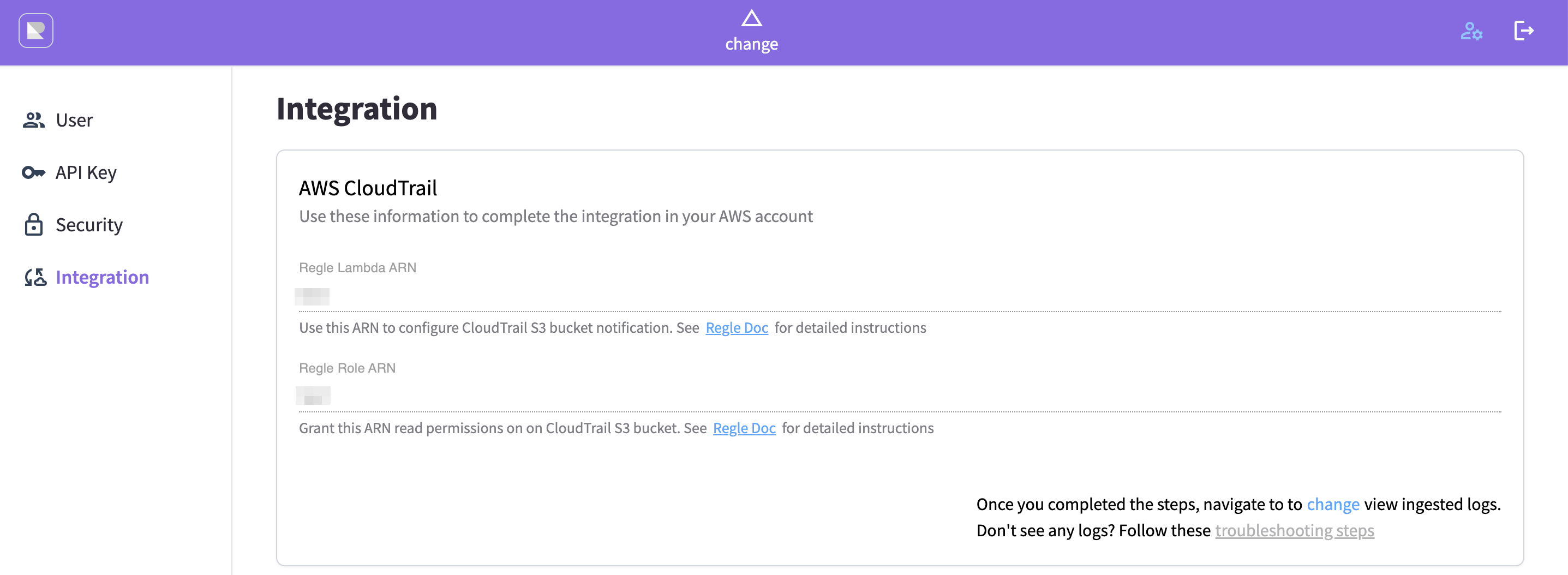
You will need these information to give Regle's permission to your CloudTrail S3 bucket. See next step.
3. Configure CloudTrail S3 Permission
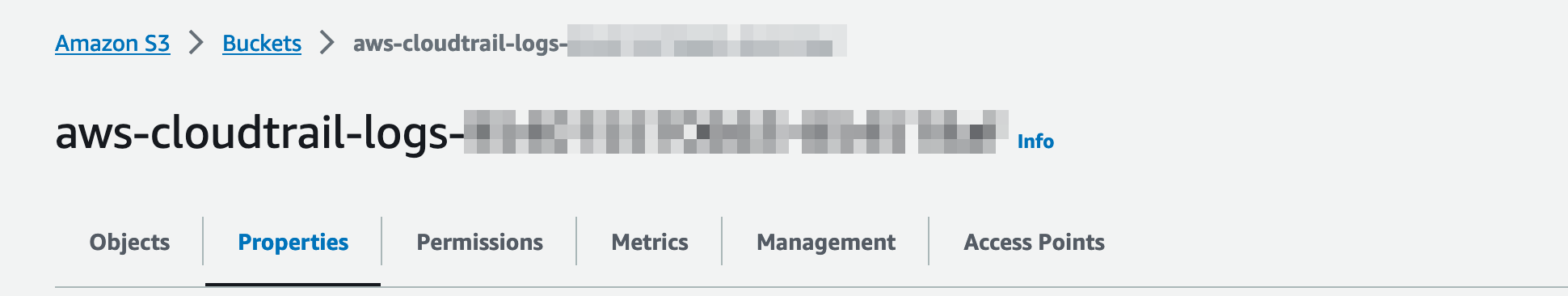
Navigate to your S3 bucket hosting your CloudTrail logs.
Enable S3 Notification
Under Properties tab, find Event Notification and click Create Event Notification.
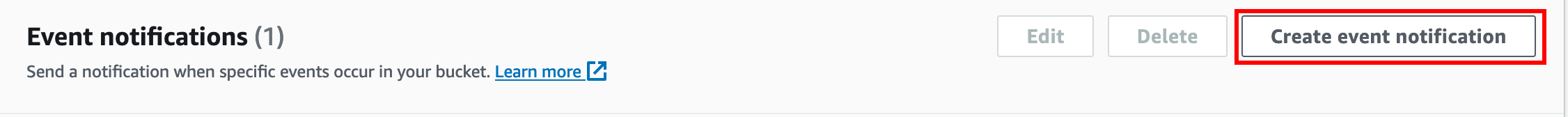
In the Notification UI, provide a name (ex "regle-integration") and under Event Types, select "All object create events".
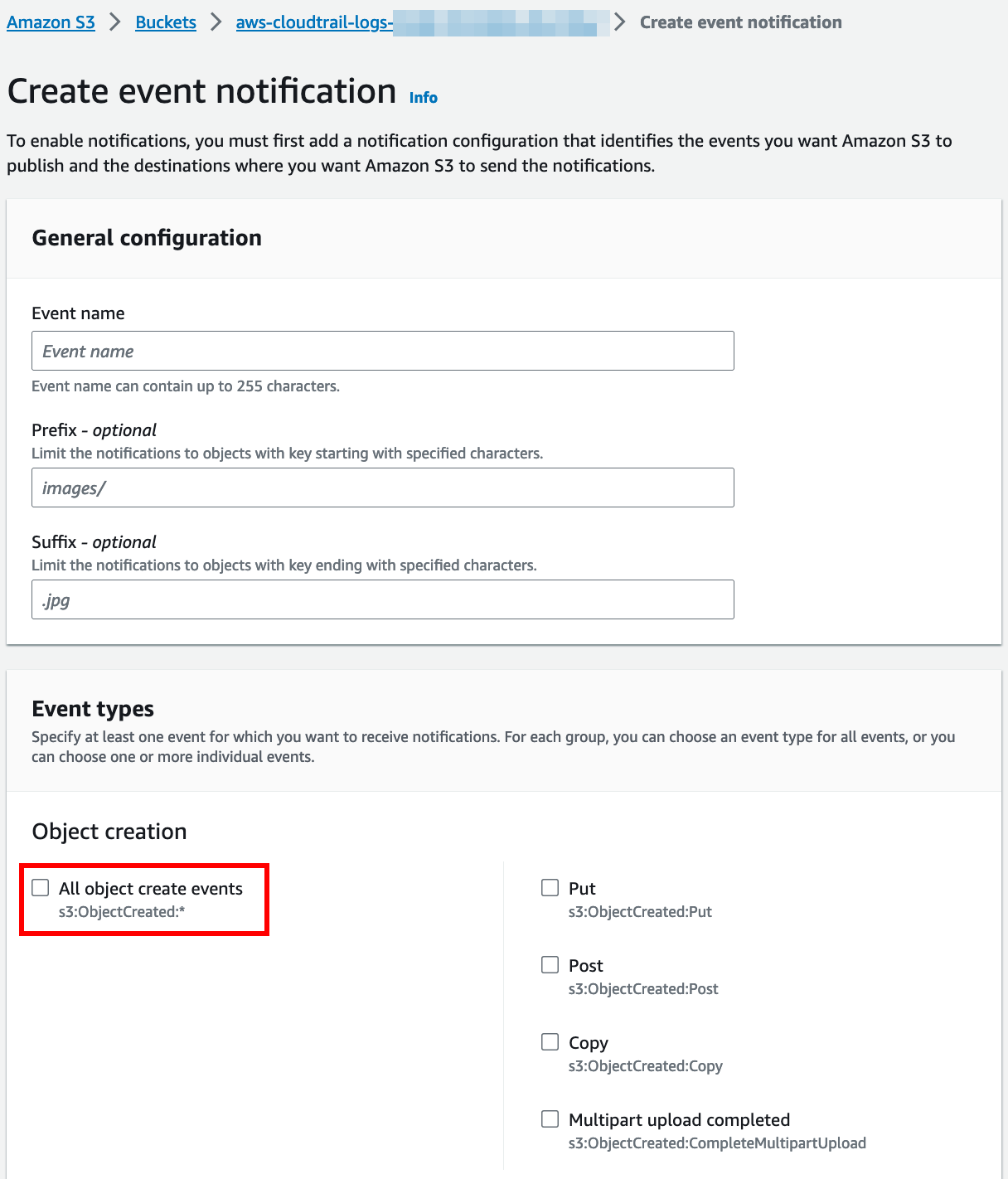
Scroll to the bottom and under Destination section, choose Lambda and provide Regle's Lambda ARN from step 2.
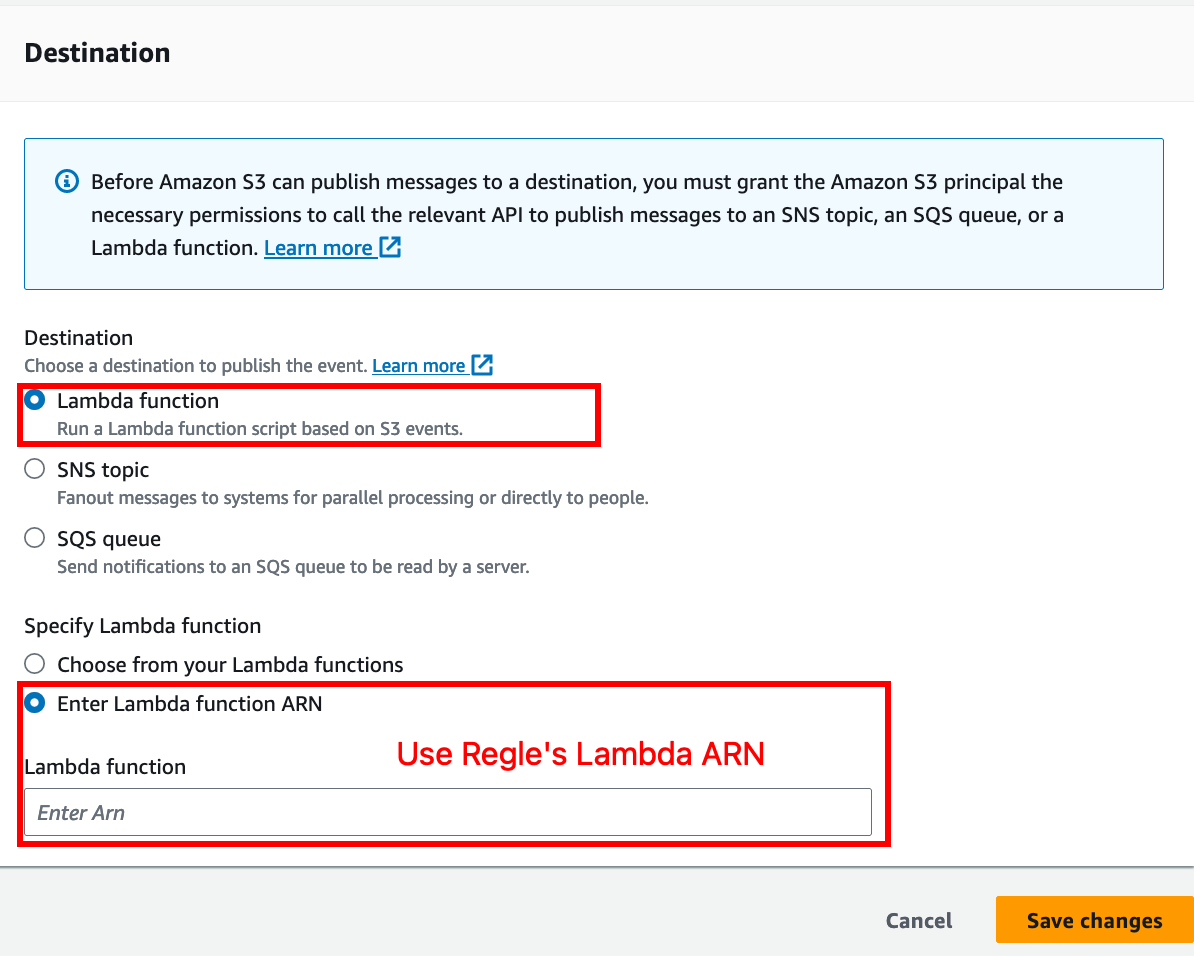
Finally, click "Save Changes".
GetObject Permission
Under Permission tab, find Bucket Policy and click "Edit"
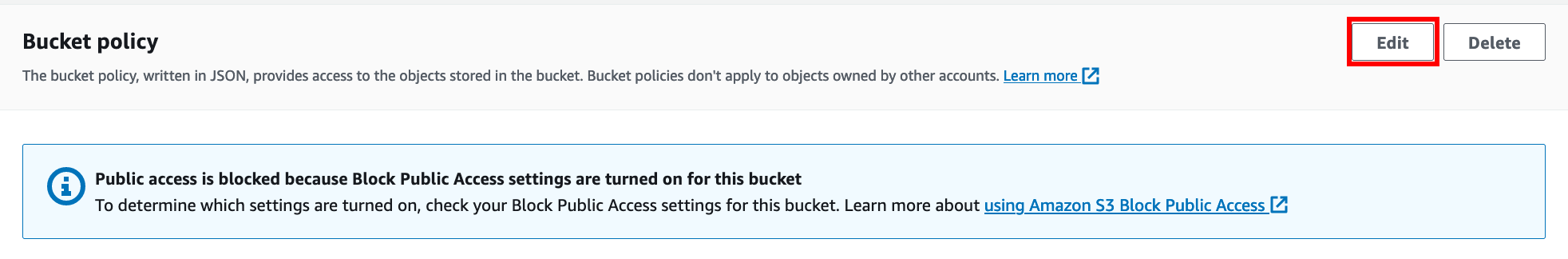
and paste in a policy similar to below
{
"Effect": "Allow",
"Principal": {
"AWS": "<REGLE_ROLE_ARN from step 2>"
},
"Action": "s3:GetObject",
"Resource": "<YOUR_S3_BUCKET_ARN>/*"
}
and save the result.